- Joined
- Jul 4, 2006
- Messages
- 5,128
- Location
- Lincoln, Nebraska
- Display Name
Display name:
Jason W (FlyNE)
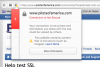
We're adding an option to access the site via SSL for those that would like to do so. After a couple of months of testing, we'll probably make it all SSL. If all of you could do me a favor and test the SSL version of the site from every browser and let me know if you have problems. Make sure that you test any issue with and without SSL before posting so that we know that it is truely a SSL issue.
I'll say right off the bat that I've got the ciphers and everything pretty tightened up on this install. It may not work in some browsers. As we get some feedback we may try to adjust it.
Non-SSL
http://www.pilotsofamerica.com/community/threads/help-test-ssl.90625/
SSL
https://www.pilotsofamerica.com/community/threads/help-test-ssl.90625/
The only difference in switching any URL on the site to SSL is just to add the 's' at the end of 'http'
I'll say right off the bat that I've got the ciphers and everything pretty tightened up on this install. It may not work in some browsers. As we get some feedback we may try to adjust it.
Non-SSL
http://www.pilotsofamerica.com/community/threads/help-test-ssl.90625/
SSL
https://www.pilotsofamerica.com/community/threads/help-test-ssl.90625/
The only difference in switching any URL on the site to SSL is just to add the 's' at the end of 'http'